Explain the Difference Between Link and End-to-end Encryption
What is the difference between link and end to end encryption. Hardware encryption devices interface with the physical layer and encrypt all data that pass through them.
Protecting Data In Transit Cissp Free By Skillset Com Youtube
You can swipe up on an existing chat to enter vanish mode which will make it so all of your messages are deleted when the chat window is closed.

. The purpose of hashing is indexing and retrieving items from the database. Encryption is always done with the intention of recovering the original information back. Hence the name end-to-end.
Which headers are left in plaintext when we use link encryption. E2EE also ensures that the plaintext entered into the encryption system is only visible to the sender and recipient. End to end indicates a communication happening between two applications maybe you and your friend using Skype.
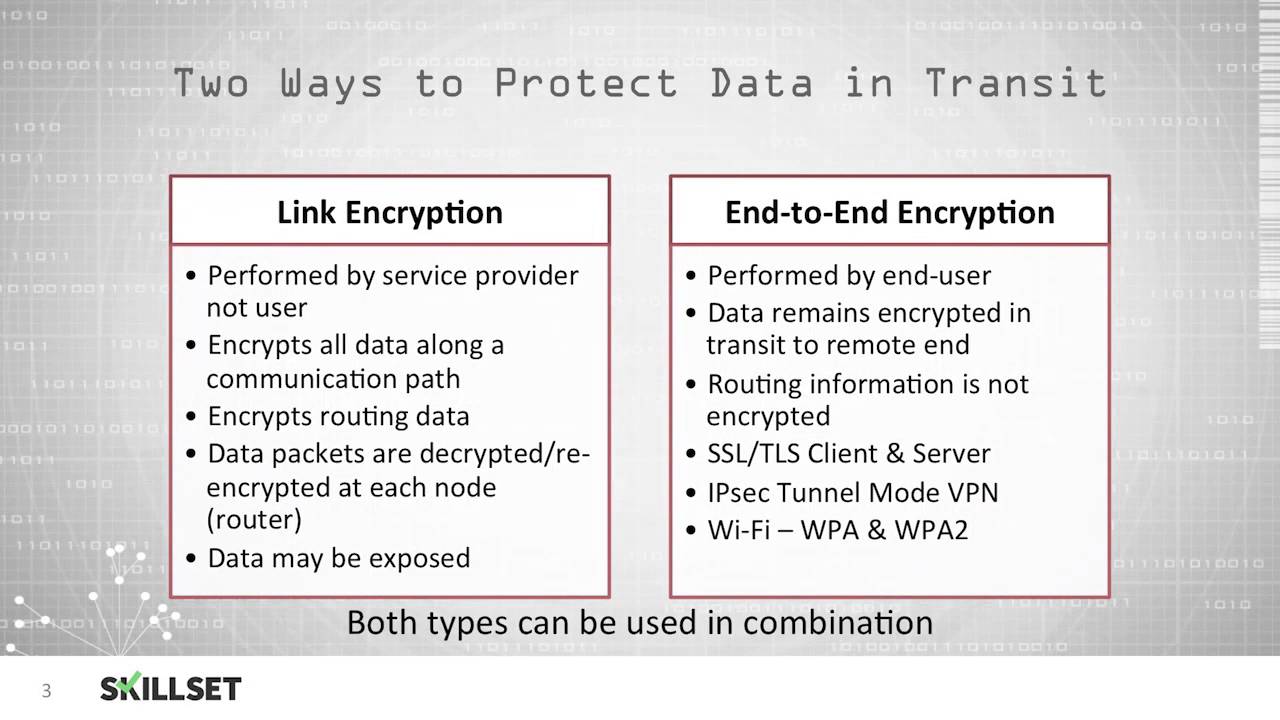
Link encryption occurs at the data link and physical layers. This means that from the moment the card is tapped on or entered into a payment terminal the data is encrypted. Encryption also allows us to recover the original information back using the corresponding encryption key.
Can someone explain or give me some documentation on how the end to end encryption work with the sync of the desktop app. Answer 1 of 6. Link encryption has to decrypt the packets at every device between the two ends.
When E2EE is used a message only appears in decrypted form for the person sending the message and the person receiving the message. Link Encryption End to End Encryption 1With link encryption each vulnerable communication link is equipped on Both ends with an encryption device 2Message exposed in sending host and in intermediate nodes 3Transperant to user 4Host maintains encryption facility. Signal lets you link the app on your phone to another device like a Windows PC Mac or iPad.
With link encryption each vulnerable the Communications link is equipped on encryption. Link encryption differs from end-to-end encryption E2EE in that with E2EE the internal message but not header and routing information is encrypted. How is end-to-end encryption different from other types of encryption.
In the world of in-person or in-store payments end-to-end encryption E2EE to its friends is the process of encrypting card-holder data for the entirety of the payments process. There is a difference between link encryption and end-to-end encryption in that link encryption encrypts and decrypts all traffic at each end of a communication line whereas with end-to-end. Encryption is the process of converting the information from one form to another using an encryption key.
This sensitive data includes the shoppers account data such as the account. One facility for ll users End to End Encryption 1. The encryption process is carried out at the two end systems the source host or terminal encrypts the data.
There is a difference between link encryption and end-to-end encryption in that link encryption encrypts and decrypts all traffic at each end of a communication line whereas with end-to-end. Can be done in hardware 5. The objective of P2PE and E2EE is to provide a payment security solution that instantaneously converts confidential payment card.
Link Encryption 1. The end to end encryption means that Mega pretty much cant narc on you no matter how much pressure its under. Explain the difference between passive and active attacks on a network.
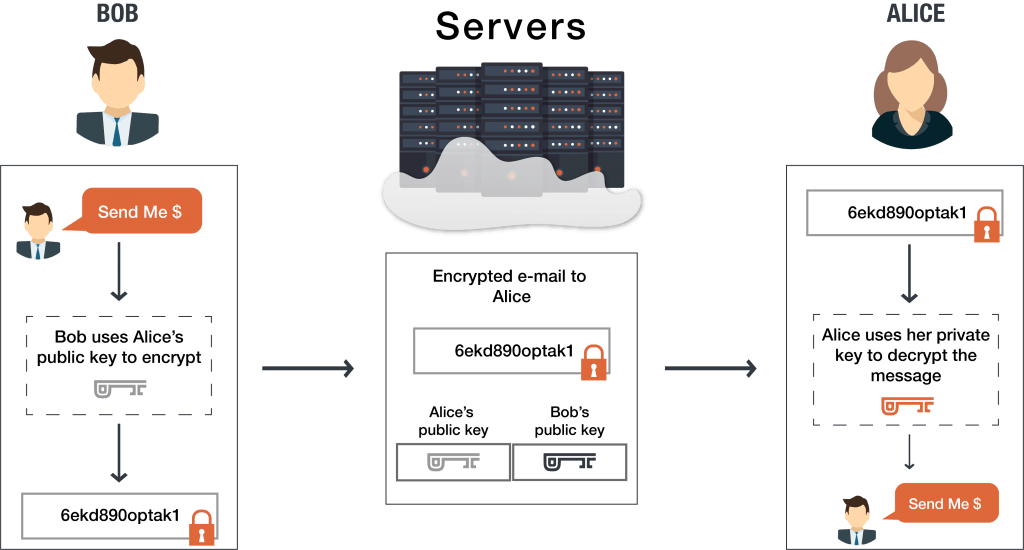
Point-to-point encryption P2PE is a standard established by the PCI Security Standards CouncilPayment solutions that offer similar encryption but do not meet the P2PE standard are referred to as end-to-end encryption E2EE solutions. End-to-end encryption E2EE is a type of messaging that keeps messages private from everyone including the messaging service. With end to end encryption the encryption process is carried out at the t o end system.
Any image link or discussion of nudity. The hash code or key can not be reversed to the original information by. Any behavior that appears to violate End user license agreements including providing product keys or links to pirated software.
Give an example of each. Any behavior that is insulting rude vulgar desecrating or showing disrespect. It was the only type of encryption in use prior to the development of public-key encryption.
PGP but you do need to work out how to transport the key for decryption which is a possible weak link. Unsolicited bulk mail or bulk advertising. The data in encrypted form are then transmitted unaltered across the.
Each vulnerable communications link is equipped on both ends with an encryption device End-to-end encryption. Link encryption differs from end-to-end encryption mainly in the fact that it encrypts and decrypts all traffic at every point no just at the end points. You can carry on your conversations between multiple devices without sacrificing end-to-end encryption as you would have to do.
End to End can be just as effective eg. It doesnt care whats in the middle it just consider that the two ends. Theres also Secret Conversations which is used by clicking the lock when you create a new chat.
There is a difference between link encryption and end - to - end encryption in that link encryption encrypts and decrypts all traffic at each end of a communication line whereas with end - to - end encryption the message is encrypted by the sender at the point of origin and only decrypted by the intended reader Link 2006. Provides host authentication 4. There are two ways to use Messengers end-to-end encryption.
At what layer does it take place. I will describe this simple and short. Encryption is a two-way process.
Wiki makes it sound like point to point is better this is due to the work that has been put into TLS Transport Layer Security so that your https traffic is secure. Conventional encryption is a cryptographic system that uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. What is the difference between link and end-to-end encryption.
The sender is one end of the conversation and the recipient is the other end. With this approach all data is in an encrypted state while it travels on its communication path. It wont know what youre storing on.
The process is very fast. Transperant to ser 3. It is called end-to-end encryption because the message stays encrypted from one end of its journey to the other.
The purpose of encryption is to transform data to keep it secret from others. I understood thats the encryption is the main advantage on telegram security related since telegram can only do e2e between phones and when having secret chat rest is unencrypted. Signal was designed from the ground up for end-to-end encryption so it can optionally sync end-to-end encryption between your devices.
It is still much preferred of the two types of encryption systems due to its simplicity. As far as what encryption actually.
End To End Encryption And Guide On How It Works Preveil

0 Response to "Explain the Difference Between Link and End-to-end Encryption"
Post a Comment